Amnezia VPN review 2024
Amnezia VPN review 2024
1. About the company
2. Pricing
3. Privacy
4. Protocols
5. Setup and configuration
6. Anti-censorship tools
7. Performance
8. Conclusion
I’m usually quite suspicious of free VPNs, especially ones with such bold claims about their privacy stance. Usually, all it takes is a visit to their privacy policy to find that the VPN is subsidized by intrusive data-scraping or, even worse, ads inserted directly into your browsing traffic. When I saw that Amnezia VPN advertised itself as a free service, I immediately started looking for the catch.
I was pleasantly surprised by the fact that Amnezia VPN seems to be taking a totally different approach. It’s an open-source solution built by a Russian team in collaboration with Privacy Accelerator, an organization dedicated to funding and developing privacy tools for use inside Russia. Without diving too deeply into the politics, Russia’s increasingly hostile stance towards free speech necessitates the use of the best VPNs around to communicate without worrying about prying eyes reading over your shoulder - or worse.
About the company
The Amnezia team released a completely open-source and decentralized VPN solution to combat Russia's harsh censorship. It isn’t decentralized in the Web 3.0 sense of the word, where everyone contributes their bandwidth to a single VPN network, but decentralized in the true sense of the word: there is no “Amnezia network”.
Let’s get this out of the way: Amnezia is not a one-click VPN solution. In fact, the Amnezia team doesn’t host their own servers at all. They’ve instead released a VPN product that allows you to deploy your own customized VPN server on the hosting site of your choice. While they recommend several known hosting providers, including Amazon AWS and Digital Ocean, you’re entirely free to pick whichever host you want. In theory, you should even be able to host a VPN off of your domestic internet connection.
So, if Amnezia doesn’t host a VPN service for you, what does it do? Well, Amnezia takes a lot of the difficulty of running a secure VPN server out of your hands. If you’re worried about a third party reading the data you route through a VPN, Amnezia lets you take back control by running your own VPN server. As long as you trust your host, you’re in complete control of how your server works.
Amnezia VPN pricing
Amnezia is completely free—that’s free as in free speech, and the client and server source codes are available on the GitHub repository for anyone to download. You don’t need to pay a penny to download the product and you’re able to modify and redistribute it as you wish.
Amnezia is also licensed under GPLv3, which means that it’s a breach of the license to use the Amnezia code as the basis for your own paid white-label VPN service. Other than that, you’re free to do anything you like with the code as long as you continue to distribute it with a GPLv3 license and don’t charge users.
The Amnezia project is funded by a combination of donations from various sources and contributions from non-profits through the Privacy Accelerator project. If you’re interested in chipping into the project, you can subscribe to the Amnezia Patreon or donate through Bitcoin, Monero, or Payeer.
Does Amnezia VPN offer privacy?
The real appeal of Amnezia is unparalleled control over your data. Even the most bullet-proof VPN solutions require you to trust your provider to protect your data from external hackers and their own employees. With Amnezia, you can pick the server host you have the most confidence in, and keep the administration of your own VPN server entirely in-house.
I particularly like how Amnezia handles DNS leaks. If you’re using a VPN while browsing the web, and if your DNS requests are still going through your ISP’s DNS servers, you’re actively disclosing the domain of every website you visit to your ISP (and thus, the government). Amnezia solves this issue by providing an interface allowing you to install your own DNS server on your hosting of choice, minimizing the amount of data you leaking while browsing.
Plus, Amnezia isn't interested in keeping, collecting, or storing logs, claiming:
"You have full control over your data. The app does not collect or transmit any statistics, logs, or other information about users or their data."
Amnezia VPN protocols
When you’re installing Amnezia, you’re presented with a choice of server settings based on the severity of censorship in your country. It's pretty much just a novel way to pick the protocols installed on your VPS by default, but, it's nice to see that it’s couched in language a non-specialist will understand.
Disclosing that you’re under extreme censorship will install OpenVPN over Cloak, medium censorship uses a hardened version of WireGuard, and low censorship will install default WireGuard.
Choosing to install your own VPN protocol instead lets you choose between default OpenVPN, OpenVPN over ShadowSocks, and IKEv2. All of these protocols are highly secure but differ in terms of connection speed and how obviously they appear as VPN traffic when analyzed.
IKEv2, OpenVPN, and WireGuard are all easily detected by basic deep package inspection (DPI) techniques and, as such, are only offered for the sake of encrypting your data. Any ISP looking to block your VPN traffic will shut down the connection to your VPN server, even if you’re also running an obfuscated VPN service. Instead, I’ll look at Amnezia’s obfuscated protocols and how well they hold up.
Without access to Russia or China’s internet routers, it’s difficult to truly tell how well a VPN protocol holds up under scrutiny. With that said, there are multiple techniques you can use to identify VPN traffic and it’s possible to make educated guesses about how governments track VPN usage.
The most obvious one is comparing against a list of known VPN servers. This could involve using the VPN service and enumerating endpoint IP addresses assigned to you, or accessing a third-party IP database of known VPN addresses. It’s not a comprehensive solution but it’s a good start for any authoritarian government. It works against commercial VPNs, but Amnezia skirts this problem by letting you host your own VPN—any hosting site could be a VPN, and it would simply be unfeasible to block every hosting site without making the internet completely unusable.
Curious about VPN protocols? Or want to figure out which one is your match made in heaven? Check out our guide to VPN protocols.
An ISP could also block the default port numbers for VPN protocols. OpenVPN and WireGuard both connect to a fairly unique default port, but this isn’t a particularly effective solution. By changing the port to something another ubiquitous web service uses (such as 443 for HTTPS), you can ensure your VPN traffic can’t be blocked at the port level without forcing an ISP to block the other services associated with that port, again, making the internet completely unusable.
Both of these techniques are somewhat rudimentary and don’t address the actual problem: DPI. OpenVPN and WireGuard traffic can be identified by looking at the structure of the packet headers, which have a distinct set of bytes. You can try this out for yourself by opening up WireShark and capturing some traffic with WireGuard open. You’ll see that the first byte in the WireGuard header is either “01”, “02”, “03”, or “04”, each corresponding to a type of WireGuard packet, followed by three bytes of “00”. A DPI program can match these bytes to instantly determine whether this is a WireGuard packet without reading the inner contents. From there, it’s as simple as null-routing the destination of the packet, and now your WireGuard connection no longer works. A similar concept applies to OpenVPN.
This means there’s a flashing arrow over every VPN packet you send that says “Hey, I’m a VPN packet!”. It’s not hard for your ISP to capture this information. Amnezia employs some interesting ways to avoid classification, but let’s finish discussing the ways an ISP can identify VPN traffic with the most nebulous, and least understood method: behavioral analysis.
The frequency, size, and destination of individual packets can be aggregated to create a statistical profile of a user’s internet traffic. Then, this reveals information about the stream of traffic, even if it's encrypted and obfuscated. Neural networks can be trained to accurately identify OpenVPN traffic with over 90% success rates. The entropy of an encrypted message can be analyzed to decipher which file type it might be, too. These are just the techniques we’re aware of, but many DPI vendors use black-box software to analyze traffic and this is especially true of ISPs in repressive regimes.
It’s not all doom and gloom, however. Security is always an arms race, even when it seems dismal for one side. Amnezia offers several different obfuscation methods with different levels of success against DPI. OpenVPN over ShadowSocks is the most well-known... and least effective. It creates an encrypted connection to a SOCKS5 proxy server, allowing you to run a VPN over the connection which doesn’t show any tell-tale signs of VPN use.
Unfortunately, the behavioral analysis I talked about earlier exposes ShadowSocks. It’s hard to find concrete details on how China blocks this system, but chatter amongst VPN circles suggests it’s fallen out of use and authorities are starting to use it to identify connections. This is backed up by the existence of SSAPPIDENTIFY, an academic project published by Xidian University, China, which seeks to classify types of ShadowSocks application traffic by using neural network classification. There are also suggestions that ShadowSocks is now vulnerable to active probing, whereby an ISP will send crafted traffic to a suspected ShadowSocks server and analyze the response to determine whether it’s really a ShadowSocks server.
Thankfully, ShadowSocks now supports plugins that enhance the usability of the project as an obfuscation tool. Cloak is the most important one offered by Amnezia, as it drastically reduces the protocol's vulnerability to active probing methods while continuing to masquerade as HTTPS traffic not easily identified by traditional DPI methods. Cloak does significantly downgrade the speed of your internet connection, but it’s worth it if you’re extremely concerned about the security of your internet traffic.
Finally, we get to Amnezia’s custom implementation of WireGuard: AmneziaWG. It’s important to note that AmneziaWG is not Amnezia’s recommended solution for extreme censorship, which is OpenVPN over Cloak. Instead, AmneziaWG is a hardened version of WireGuard that removes several key aspects used to identify WireGuard using traditional DPI methods. It changes the header values from the static ones I outlined earlier to random values, which makes it harder for DPI to identify the WireGuard packet. WireGuard packets also have a static size of 148 bytes, but AmneziaWG appends junk data to the start of a packet to randomize the packet size, making packet matching harder. Finally, the initial session connection is disguised by sending junk packets at the start of the connection. Honestly, it’s unclear if this would make a massive amount of difference to traditional DPI methods but potentially confuse statistically-based behavior analysis.
You should note that all of these obfuscation techniques add additional overhead when using WireGuard proportional to how much junk data you’re adding on a per-packet basis. All of these metrics are customizable from inside the Amnezia app, so you can balance obfuscation against speed until you find a sweet spot that confuses DPI while keeping your connection usable. While I don’t have a Russian or Chinese ISP to test against, it wasn’t possible to create a set of rules in WireShark that could accurately characterize AmneziaWG traffic without prior knowledge of user settings. Amnezia’s own testing in these regions suggests that any regime that outright drops unfamiliar UDP traffic will filter out AmneziaWG traffic, so where possible you should probably stick to the slower OpenVPN over Cloak protocol. However, for regimes with less advanced DPI, such as Iran, Egypt, and Turkey, it may be a viable solution. Your mileage may vary.
Amnezia VPN setup and configuration
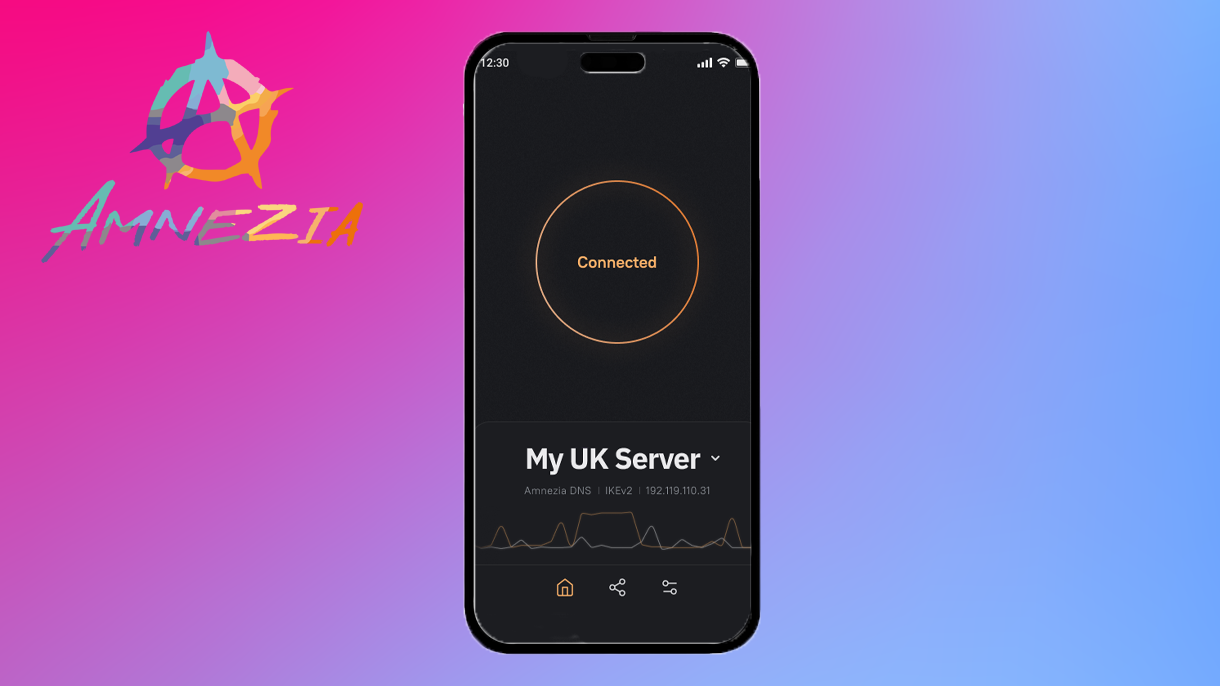
Amnezia makes server administration surprisingly simple, too. You set up a VPS server on your account and provide details to the Amnezia app, which you’ll have set up on your phone or desktop. Once the app logs into your VPS provider for the first time, it sets up the relevant public key infrastructure and OpenVPN key-pair necessary to authenticate you securely in the future. The client then connects by SSH and automatically installs and configures the Docker software required to run your VPN connections.
We used Amnezia VPN to set up a VPN server from scratch—and the result was pretty awesome.
Each time you start a new VPN protocol connection, your Amnezia client boots up a new Docker instance with randomly generated SSH keys. This approach has two major benefits: any data left behind by your VPN instance is removed from the server after your connection is terminated, and any new instances have completely fresh credentials. If you’re worried your key has somehow been compromised, you can tear down your Amnezia instance and start a new one in just a few moments.
After you’ve started up an Amnezia instance, all admin is taken care of inside the app. Installing new protocols on your server, sharing your access credentials with others, and adding new servers to your client only takes a few taps. It makes tweaking your VPN service shockingly easy and I’m impressed with how seamless this process is. It’s clear that Amnezia’s team put thought into creating a user-friendly product that’s still powerful enough to provide effective security while browsing.
Amnezia anti-censorship tools
Amnezia also recently announced the launch of its anti-censorship tool, available in Russia, Myanmar, Iraq, and Kyrgyzstan, at no extra cost.
These four countries have been hit particularly hard by censorship, making it increasingly difficult for citizens to access sites and services like Facebook, X, WhatsApp, and TikTok. It's easy to take these platforms for granted, but they're vital sources of information, allow folks to keep up with current events, and a means to stay in touch with friends and family.
Amnezia's tool allows access to sites that'd otherwise be inaccessible, thanks to censorship.
- In March 2022, Russia blocked independent media outlets covering the Ukraine war, including the BBC and Deutsche Welle, as well as popular social media platforms. Amnezia worked alongside Russian human rights activists, Roskomsvoboda, to release the first version of the service.
- In 2021, following a military coup, Meta services were blocked in Myanmar. Fortunately, the Amnezia service arrived in the country in April 2024.
- Kyrgyzstan blocked TikTok back in April 2024, though citizens can now regain access to the app via Amenzia.
- Amnezia introduced its tool into Iran in May 2024, too, using the AmneziaWG protocol—a necessity, given that all standard VPN protocols are blocked in the country.
Performance testing: How fast is Amnezia VPN?
Ultimately, your speed and streaming capability will vary massively depending on which host you use and how far away you are from it. For this reason, it’s hard to come up with meaningful numbers, because your experience is absolutely going to be different from mine.
What you should keep in mind is that Amnezia is not an ideal solution for unblocking content streams such as Amazon Prime or Netflix, as these providers are constantly on the lookout for non-residential access to their streams and block those IPs accordingly.
Amnezia VPN review - final verdict
It could be said that there’s nothing fundamentally innovative about Amnezia VPN—after all, what’s stopping you, a tech-savvy internet user with unfiltered website access from registering a VPS subscription and installing some open-source VPN software yourself?
If that’s your takeaway from Amnezia VPN, you’re missing the point. Not everyone has the knowledge or resources to set up a micro-VPN service securely, but everyone should have access to a free and unfiltered internet. It shouldn’t be an exercise in gatekeeping, where only the most well-read and capable internet users can duck past censors. Privacy tools need to be easy to use to keep the barrier to entry as low as possible. This philosophy is baked into Amnezia’s design all the way through. You can even share your VPN client information with other users through the app so it’s possible to run a single VPN server for several of your friends and family with relative ease.
Amnezia embraces this philosophy wholeheartedly with a simple interface and clear, concise support material that walks you through the installation process in plain English. I can’t speak for how the site reads in Russian, but I can only assume it’s similarly well-written. The source code for both client and server has been independently audited by 7ASecurity, which published several exploits of varying severity that the Amnezia team has patched. This approach to transparency is really refreshing from a VPN provider.
The only significant issue I can see with Amnezia is that you’re handing over your server credentials to a third party, which automatically administers a server for you. Normally, this is a setup I’d balk at. However, the Amnezia app and server are both fully open-source. You can browse the source code line by line for yourself if you need convincing that Amnezia isn’t malicious.
I can only think of one other solution that’s attempting to do something similar to Amnezia, and that’s Outline VPN from Jigsaw, a Google technology incubator dedicated to technology projects that intersect with online anonymity and freedom of speech. It uses ShadowSocks to tunnel a ChaCha20 encryption stream, but it’s not as pointedly designed to evade DPI as Amnezia is, nor is it nearly as user-friendly. Although Outline is also open source, Jigsaw’s proximity to US defense projects makes me somewhat uncomfortable so when it comes down to it, I’d bet on the rag-tag group of Russian privacy advocates in the long run.
What's Your Reaction?



























![Netflix Horizon Zero Dawn TV Show Reportedly In Trouble [Update]](https://i.kinja-img.com/image/upload/c_fill,h_675,pg_1,q_80,w_1200/cc9a42c0341c691ff31e3f12daeddc34.jpg)



/cdn.vox-cdn.com/uploads/chorus_asset/file/25282308/247015_Evie_Ring_AKrales_0051.jpg)